January 2017 mobile malware review from Doctor Web
January 31, 2017
In the first month of 2017, Doctor Web security researchers detected an Android Trojan that infiltrated the Play Store running process and stealthily downloaded Google Play applications. Later, security researchers examined an Android banker whose source code was published online by cybercriminals. Also in January, another Android banker was detected; it was distributed as the game Super Mario Run which is not yet available for Android devices. In the last month, a new ransomware Trojan was also detected in Google Play; it blocked the displays of Android smartphones and tablets.
Principal trends in January
- The detection of an Android Trojan that infiltrated the Play Store running process and covertly downloaded applications from Google Play
- The distribution of new banking Trojans
- The detection of a ransomware Trojan on Google Play
Mobile threat of the month
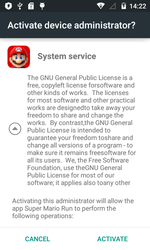
Early in January, Doctor Web security researchers detected the Trojan Android.Skyfin.1.origin, which infiltrated the Play Store running process, stole confidential information, and stealthily downloaded Google Play applications artificially increasing their popularity. Android.Skyfin.1.origin has the following characteristics:
- it is distributed by other malicious programs that try to get root privileges and install the Trojan in the system directory;
- it steals authorization data and other confidential information from Play Store by simulating its operation and downloads applications from Google Play without user knowledge;
- after applications are downloaded, it saves them on an SD card but does not install them so as not to arouse the suspicion of the owner of the compromised mobile device;
- it leaves fake reviews on Google Play for applications indicated by the cybercriminals.
For more information regarding this Trojan, refer to the article published by Doctor Web.
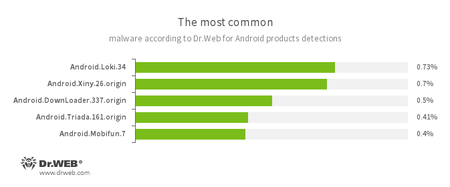
According to statistics collected by Dr.Web for Android
- Android.Loki.34
A malicious program designed to download other Trojans. - Android.Xiny.26.origin
A Trojan that downloads and installs various applications and displays advertisements. - Android.DownLoader.337.origin
A Trojan designed to download other malware. - Android.Triada.161.origin
A multi-component Trojan that performs different malicious functions. - Android.Mobifun.7
A Trojan designed to download other Android applications.
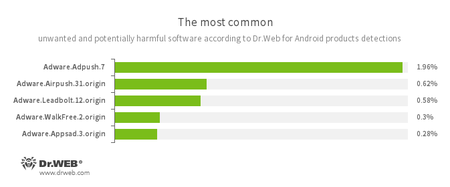
- Adware.Adpush.7
- Adware.Airpush.31.origin
- Adware.Leadbolt.12.origin
- Adware.WalkFree.2.origin
- Adware.Appsad.3.origin
Unwanted program modules that are incorporated into Android applications and are responsible for displaying annoying ads on mobile devices.
Banking Trojans for Android
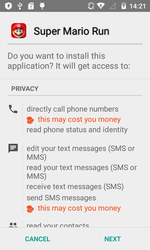
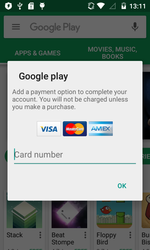
In January, the banking Trojan Android.BankBot.140.origin was detected; it was distributed by the cybercriminals as the game Super Mario Run. It is currently available only for iOS-based devices; therefore, by employing such a scheme, cybercriminals have increased the possibility that users interested in the game will install the malware.
Android.BankBot.140.origin tracked the launch of banking applications and displayed on top of them a phishing input form for entering logins and passwords in order to access user accounts. Furthermore, when Play Store was launched, the Trojan attempted to steal bank card information by displaying the phishing dialog of the Google Play purchase settings.
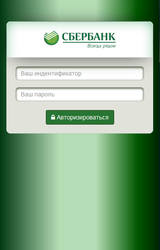
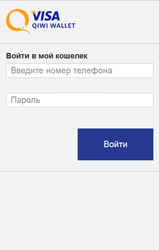
In the middle of the month, Doctor Web analysts detected the banking Trojan Android.BankBot.149.origin, which had its source code published online by cybercriminals. This malware tracked the launch of applications used to access remote banking and payment services and displayed on top of them a fraudulent form for entering user account logins and passwords. In addition, Android.BankBot.149.origin attempted to get bank card information by displaying a phishing dialog on top of Play Store.
This Trojan also intercepted incoming SMS messages and tried to hide them, tracked the infected device’s GPS coordinates, stole information from the contact list, and could send messages to all the available numbers. For more information regarding Android.BankBot.149.origin, refer to the news article published by Doctor Web.
Trojans on Google Play
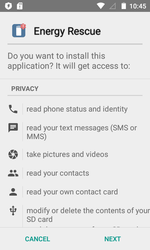
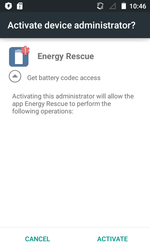
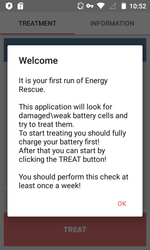
In the past month, the ransomware Android.Locker.387.origin was detected on Google Play; it served to complicate the detection procedure and was protected with a special packer. Nevertheless, Dr.Web for Android successfully detects it as Android.Packed.15893. This Trojan was distributed as the program Energy Rescue which supposedly optimized battery performance. After being launched, Android.Locker.387.origin prompted the user to grant it administrator privileges for the mobile device and blocked the infected smartphone or tablet, demanding a ransom to unlock it. However, the ransomware did not attack the devices of users from Russia, Ukraine, and Belarus.
Besides blocking Android devices, Android.Locker.387.origin stole contact list information and all the available SMS messages.
Cybercriminals are still interested in Android devices and create numerous malicious programs for this mobile platform. To protect smartphones and tablets, it is recommended that Dr.Web for Android be installed as it successfully detects Android Trojans and other malware.










![[WebIQmeter]](social/webiq.png)
![[Rutube]](social/rutube.png)
![[You Tube]](social/youtube.png)
![[Twitter]](social/twitter.png)
![[Facebook]](social/facebook.png)
![[Vkontakte]](social/vkontakte.png)
![[Одноклассники]](social/odnoklassniki.png)
![[Instagram]](social/instagram.png)
![[Pinterest]](social/pinterest.png)